Our ISO 27001 Audit Used to Be a Six-Week Fire Drill. Now, It’s a 30-Minute Coffee Break
We stopped treating compliance like a chore and started treating it like an engineering problem. The result was engineers working on the core product.
That pre-audit email. If you run a self-hosted SaaS, you know the one. The subject line “ISO 27001 Surveillance Audit Scheduled” hits your inbox, and suddenly, your company’s next month is booked.
For us, it used to trigger a full-blown fire drill. An all-hands-on-deck scramble to find proof that we’d been following our own rules. It meant pulling engineers off product development to sift through server logs, manually screenshotting configurations, and piecing together a story for the auditors. It was a month of high-stress, low-value work.
We realized this approach was fundamentally broken. We’re engineers. We build automated systems to handle complexity. Why were we tackling one of our most critical, trust-building functions with brute force and spreadsheets?
This led to a new mission: to build a compliance machine. A system that would make evidence gathering a passive, continuous background process. Our goal was to make the annual audit a non-event—a brief, confident presentation of facts.
We succeeded. And in the process, we built something other companies shouldn't have to build themselves.
From Chore to Code: A New Compliance Manifesto
The first step wasn't about technology; it was a change in philosophy. A dashboard is just a window. A tool can't make you compliant if your foundation is weak. We committed to a "Compliance as Code" approach, which meant our Information Security Management System (ISMS) had to be rock-solid first.
Policies as Blueprints: We didn't just write policies; we treated them as the official blueprints for our automated systems. From vulnerability management to access control, the policy dictated the automation.
Process over Panic: We defined and ticketed every recurring security task. Quarterly access reviews aren't something we remember to do; they are a scheduled, automated process that creates its own paper trail.
Communication is Key: We wired our security systems directly into our company's formal communication channels. A critical alert doesn't just light up a dashboard; it fires a time-stamped email to the security team, kicking off an auditable, trackable response from the very first second.
We decided that our compliance program shouldn't be something we prove once a year. It should be something we can observe, live, at any second of any day.
The Anatomy of Our Automation Engine
Our system is composed of three interconnected layers, working together to collect, analyze, and present our compliance posture in real-time.
1. The Foundation: Continuous Evidence Capture
To prove anything, you need data. We deployed the universal Grafana Agent across our entire infrastructure using Ansible for consistent configuration. This agent acts as our nervous system, constantly feeding two streams of information into our centralized monitoring stack:
Metrics via Prometheus This gives us the high-level, time-series view. Are our systems healthy? Are resources within limits? This is our operational heartbeat.
Logs via Loki: This is our forensic diary. Immutable, context-rich logs that tell the story of who did what, and when.
We capture everything, with a specific focus on what an auditor needs to see:
Linux System Integrity (
auditd) We log every modification to user accounts and, critically, any change to privilege-granting files like/etc/sudoers.Network and Server Access (
UFW/sshd) Every blocked connection attempt and failed login is captured, providing a clear view of our defensive perimeter.Automated Security Scans Nightly scans using Trivy (for software package vulnerabilities) and Lynis (for OS hardening) pipe their findings directly into our log storage.
Backup Verification Our backup scripts don't just run; they report. Every success or failure is logged, creating an undeniable record of our data protection strategy.
2. The Watchtower: Intelligent, Real-Time Alerting
Data is useless if no one is watching. Prometheus Alertmanager is our 24/7 watchtower. It’s configured to understand our security policies and notify us the instant a significant event occurs.
If an engineer escalates their privileges with sudo to alter a production file, an email is sent.
If a nightly scan uncovers a new CRITICAL vulnerability, an email is sent.
If a database backup script fails to complete, an email is sent.
The result? Our response to any incident is documented from the moment of detection. When the auditor asks about a specific event, we don’t just have logs; we have a folder of time-stamped alerts and the subsequent response tickets.
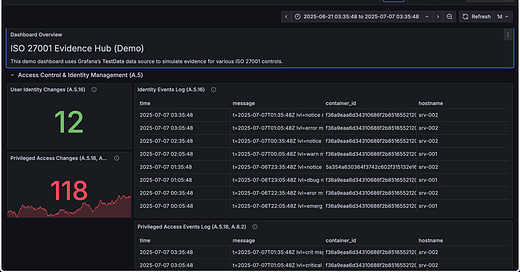
3. The Briefing Room: The Auditor's Command Center
This is where our story comes together. We built a purpose-driven "ISO 27001 Evidence Hub" in Grafana. It was designed for one audience: the auditor. There are no unnecessary engineering metrics, only clear, direct evidence.
Mapped to the Standard: Every chart and table is explicitly titled with the ISO 27001:2022 control it addresses. The auditor reads
A.8.8 - Management of Technical Vulnerabilities, and we point directly to the live table ofCRITICALfindings from our Trivy scans.Plain English Context: We added descriptions to each panel explaining why this data matters and what it proves, removing any need for technical interpretation.
The Time Machine: The dashboard’s date-range selector is our ultimate tool. “Show me your privileged access changes from Q3 last year.” Two clicks, and the entire dashboard instantly displays the requested history. No digging, no running queries, just answers.
The Audit: A Calm Demonstration, Not a Tense Interrogation
Our last audit was unrecognizable from previous years. Instead of a tense inquisition, it was a calm, collaborative walkthrough.
The auditor would ask about a control, like privileged access. We’d bring up the dashboard, point to the relevant panel, and show them not only the logs of the changes but also the automatically generated email alerts and the corresponding Jira tickets where those changes were approved.
Check. Move on.
For backups, vulnerabilities, and system logging, it was the same story. We weren't hunting for proof; we were simply presenting the living record of our operations.
### We Solved Our Headache. Now We Can Solve Yours.
In perfecting this system, we invested hundreds of hours refining Ansible roles, Grafana models, and Prometheus rules. We had built a powerful compliance engine that took the most painful part of our year and made it trivial.
We know countless other SaaS companies are stuck in that same cycle of pre-audit panic. You need to prove your security to earn customer trust, but you can't afford to derail your product roadmap for a month every year.
That’s why we’ve packaged our entire automated evidence platform. It’s a solution designed to handle the heavy lifting of technical evidence collection, getting you audit-ready in a fraction of the time and cost.
Stop dreading the audit. Let’s make it a non-event for you, too.
Reach out on LinkedIn https://www.linkedin.com/in/jknobel/
Email us: jk@datapult.dk
Buy the code: https://knobel-dk.github.io/landingpage-iso-playbooks/
We posted a similar story at https://medium.com/@accounts_73078/this-self-hosted-saas-passed-its-iso-27001-audit-heres-the-dashboard-that-did-it-ca4fccb64d23